Welcome to our discussion on API security practices! As you are aware, security is of utmost importance when it comes to developing APIs. In case you missed it, we recently published a post on API security practices. In this follow-up post, we will be delving deeper into one of the core security components - Authentication. The incoming post will cover Authorization and Data Access Control. Overall these three will help you gain a better understanding of the intricacies of API security mechanisms.
🤔 Ponder deeply about their significance before diving into the details.
The Identity Conundrum: Authentication
The Problem: In a world teeming with digital identities, how do we ensure that users are who they claim to be? This question lies at the heart of the authentication process. Without a reliable way to verify identities, the doors to sensitive information and critical functionalities could be left wide open to impostors.
📌 Before proceeding with the actual strategies, mention the most common authentication pitfalls.
🤦 Insufficient Validation - Not having an authentication at all or just relying on simple password-based systems can lead to breaches.
🤦 Hardcoding Credentials - A surprisingly common oversight is embedding credentials directly in code.
🤦 Not Using Secure Protocols - The risk of data interception is real when data is transmitted unencrypted.
🤦 Not Implementing Token Expiry and Rotation - The token is easy to misplace and therefore it is easy to abuse.
🤦 Not Rate Limiting Attempts - Someone got your user’s email and it starts iterating through the possible passwords. In some time he will crack it for sure.
🤦 Not doing Regular Audits and Updates - You’ve protected your system and think you are done for good. Not so fast mate. Attackers evolve their techniques all the time.
🤦 Custom Implementation - Authentication is ages old thing and implementing it on your own is reinventing the wheel.
🤦 Explicit user feedback - Providing detailed messages in the response, describing why the authentication failed, like invalid username, invalid password, etc.
💬 Later in the post we are going to provide remedies for each. Feel free to share your experiences and insights in the comments.
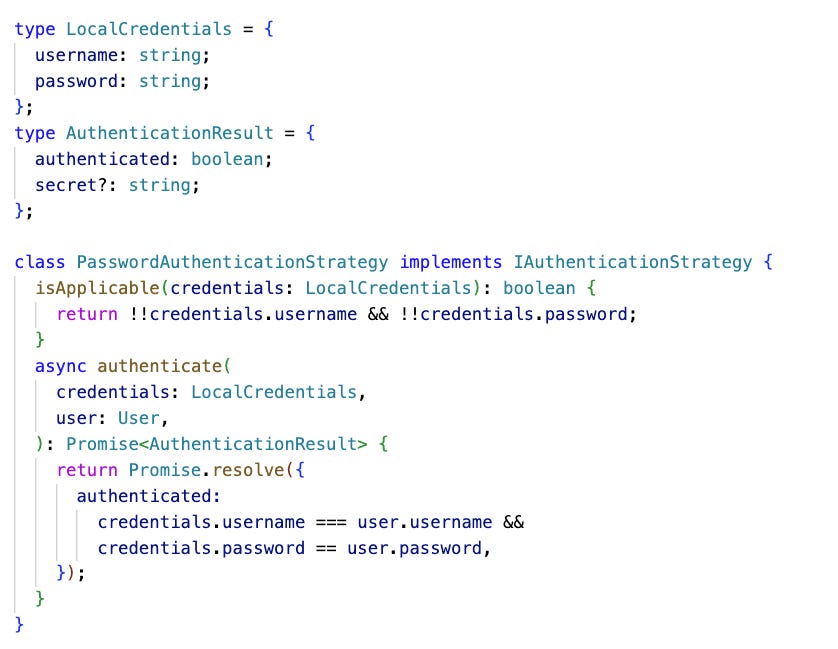
Password-Based Authentication
The most traditional form of authentication involves verifying a user based on something they know, such as a password. While common, it's essential to enhance its security through practices like hashing passwords on the server side and implementing strong password policies.
Pros & Cons:
➕ Widely understood and easy to implement
➕ Cost-effective with no need for additional hardware
➖ Vulnerable to brute force and phishing attacks.
➖ Requires strong password policies to enhance security.
When to use:
✔️ Non-critical systems with low to medium security requirements.
✔️ When simplicity and cost-effectiveness are prioritized.
✔️ As part of the more complex MFA.
Example:
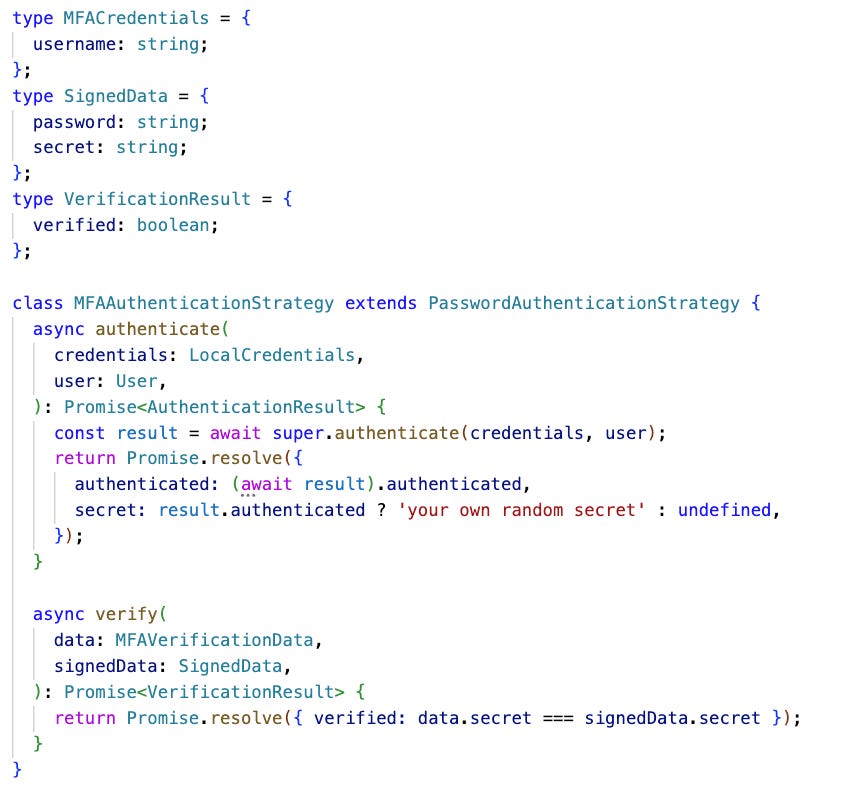
Multi-Factor Authentication (MFA)
MFA requires users to provide two or more verification factors to gain access, significantly enhancing security by combining something they know (a username and a password), with something they have (a secret code or security token) or something they are (biometric verification). This layered approach guards against unauthorized access more effectively than simple password methods.
SMS-Based and Email-Based Verification
SMS and email can be used to provide an additional layer of security by sending a one-time code to a user's mobile phone or email address, which the user must enter to gain access, although they are less secure than other methods, like biometrics.
Biometric Verification
Using unique physical characteristics such as fingerprints, facial recognition, or iris scans, biometric authentication, in the context of API security offers a highly secure and user-friendly method of second-factor verification. This means there won’t be any secret shared with the user and therefore no surface for leaks.
Pros & Cons:
➕ (MFA) Significantly increases security by adding additional verification layers.
➕ (MFA) Flexible, with various factors to choose from (SMS, email, biometrics).
➕ (SMS & Email) Simple to implement and widely accessible.
➕ (Biometrics) Offers high security and convenience with unique biological attributes, so it is difficult to forge or steal.
➖ (MFA) Can be more complex for users, potentially reducing user experience.
➖ (MFA) Reliant on user access to a secondary device or information channel.
➖ (SMS & Email) Vulnerable to interception and social engineering attacks.
➖ (Biometrics) Requires specialized hardware and can be expensive.
When to use:
✔️ (MFA) In all occasions when the stakes of potential security breaches are high.
✔️ (MFA) Where additional layers of security are necessary to protect user data and comply with legal and regulatory standards.
✔️ (SMS & Email) When there is not a short completion window.
✔️ (Biometrics) When MFA is necessary, but the speed and user convenience are also highly valued.
Example:
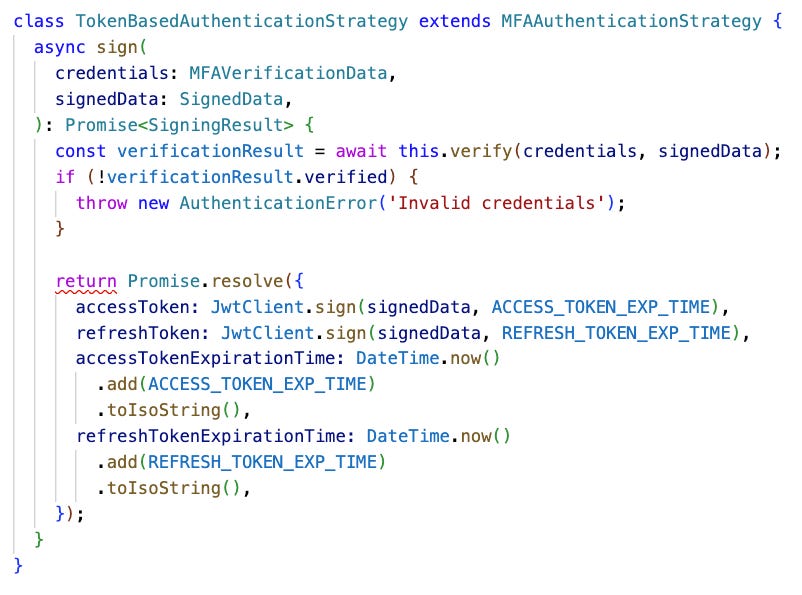
Token-Based Authentication
Token-based systems, such as JWT (JSON Web Tokens), provide a secure and scalable way to manage user sessions. After initial authentication, the server generates a token that the client uses for subsequent requests. This method is popular in RESTful APIs and single-page applications (SPAs), as it allows for stateless authentication across distributed systems.
Pros & Cons:
➕ Scalable and suitable for stateless applications.
➕ Facilitates secure API access and single sign-on (SSO) capabilities.
➖ Tokens can be intercepted or stolen if not properly secured.
➖ Requires secure management of tokens and encryption keys.
When to use:
✔️ In scenarios that require stateless authentication, where the server doesn't need to keep a record of user sessions, making it highly scalable and efficient for applications with large numbers of users or services.
✔️ Token-based authentication is ideal for single sign-on (SSO) functionalities, enabling users to authenticate once and gain access to multiple systems or applications without re-entering credentials.
Example:
OAuth and OpenID Connect
OAuth is an open standard for access delegation, commonly used as a way for users to grant websites or applications access to their information on other websites without giving them passwords. OpenID Connect, built on top of OAuth 2.0, provides an identity layer that allows developers to authenticate users. These frameworks are widely used for social logins and single sign-on (SSO) functionalities, simplifying the user experience by allowing them to use existing credentials from services like Google, Facebook, or Twitter.
Pros & Cons:
➕ Enables secure, delegated access without sharing passwords.
➕ Standardised protocols with broad support across services.
➖ Complex to implement correctly.
➖ Requires trust in third-party providers.
When to use:
✔️ It is particularly useful for implementing single sign-on (SSO) across multiple applications, enhancing user experience by enabling users to log in once and access a variety of services without repeated authentication.
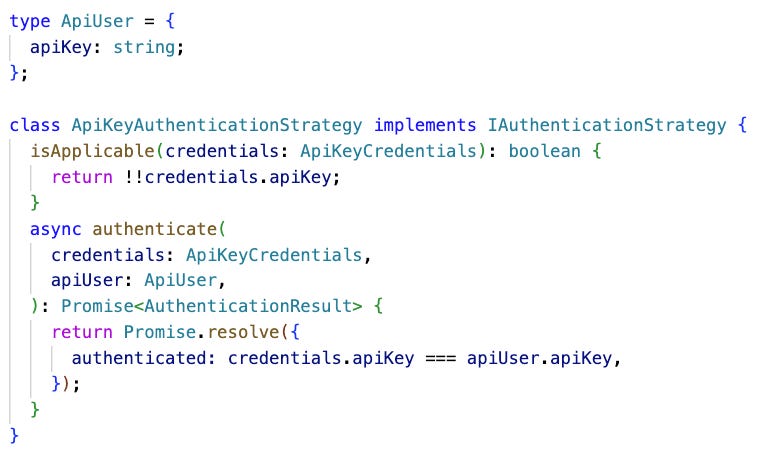
API Key-Based Authentication
API key-based authentication is a method where a uniquely generated key is sent along with API requests to authenticate the sender's identity. Each key is associated with a single consumer and it should be rotated periodically to avoid security breaches.
A common way of providing an API key is via api-key HTTP header.
url --location --request GET 'https://your.domain.com/api/v1/your/path/to-the-resource' \
--header 'api-key: <api_key>'Pros & Cons:
➕ API keys are straightforward to implement and use.
➕ Managing API keys is relatively easy, making this method suitable for both small and large-scale applications.
➕ API key-based authentication is compatible with almost any system or application.
➕ Each request made with an API key can be easily traced back to the key's owner.
➖ API keys, if intercepted, can provide full access to the associated services.
➖ Since API keys, as information included in request headers, are easily intercepted if there is no secure communication.
➖ API keys do not inherently support distinguishing between different users or sessions using the same key, making it challenging to implement fine-grained access control or personalize responses based on the user.
➖ Revoking compromised API keys can immediately disrupt the service, potentially requiring reconfiguration or redeployment.
When to use:
✔️ Service-to-service communication.
Example:
Certificate-Based Authentication
This method involves using digital certificates to authenticate users, devices, or servers, typically in environments requiring a high-security level, such as corporate networks or secure web applications. It relies on public key infrastructure (PKI) and is more complex to set up but offers a high degree of security and trust.
Pros & Cons:
➕ High security through digital certificates and PKI.
➕ Suitable for machine-to-machine authentication and secure email.
➖ Complex setup and management.
➖ Requires a trusted Certificate Authority (CA).
When to use:
✔️ This method is particularly well-suited for scenarios requiring secure, mutual authentication between clients and servers, such as in VPN access, secure email, and when establishing secure connections between IoT devices or within enterprise networks.
✔️ This form of authentication shines in applications requiring automated, secure interactions between machines, like service-to-service communication in microservices architectures, where traditional login mechanisms are impractical
📌 Solutions to the most common authentication pitfalls
💡 Insufficient Validation - Incorporate Multi-Factor Authentication (MFA) wherever feasible, especially for APIs that provide access to sensitive data or operations.
💡 Hardcoding Credentials - Utilise environment variables and dedicated secrets management tools to keep credentials secure and out of the source code.
💡 Not Using Secure Protocols - HTTPS stands as the guardian, encrypting data in transit and shielding it from prying eyes.
💡 Not Implementing Token Expiry and Rotation - Implement token expiration and rotation policies to reduce the impact of token compromise.
💡 Not Rate Limiting Attempts - Apply rate limiting to prevent abuse and mitigate brute force attacks.
💡 Not doing Regular Audits and Updates - Conduct regular security audits and update authentication mechanisms as needed to address new vulnerabilities.
💡 Custom Implementation - Leveraging existing Identity Providers (IdPs) like Auth0, Okta, or Firebase Authentication can drastically reduce the burden of building complex authentication systems from scratch, and protect you from all those things that can go wrong.
💡 Explicit user feedback - Always provide a generic message, like ‘Invalid credentials’. Along with it provide an error code that is known only to the consumer of your API, defined in private documentation, so they can map it to a user-friendly message in the consumer app.
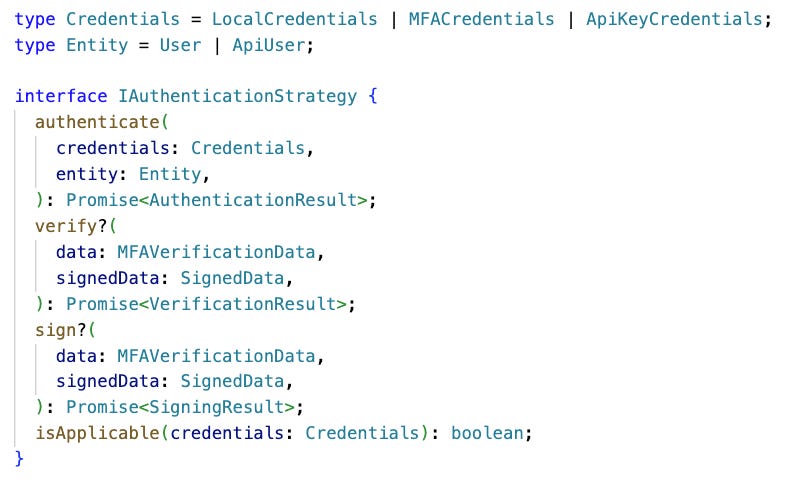
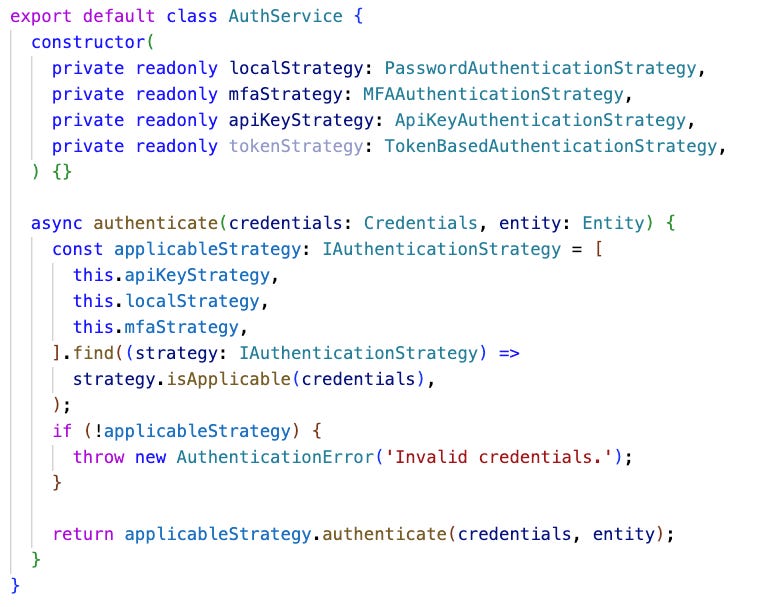
🎁 Bonus Example: Multiple authentication strategies in TypeScript
👋 Until the next time: Farewell
In this post, we've traversed the spectrum of authentication strategies, shedding light on options from the straightforward, such as password-based authentication, to more sophisticated methods like biometric multi-factor authentication. Each strategy comes with its own set of advantages, tailored to meet varying requirements around security, user experience, and operational contexts. Understanding and implementing these strategies in mobile apps and APIs is crucial for bolstering security and enhancing user experiences. By selecting the right authentication methods, developers can not only secure their applications but also build a foundation of trust and reliability.
As we look forward to our next discussions, we'll delve into the realms of Authorization and Data Access Control. Authorization is pivotal in managing user permissions and access rights, ensuring users can only perform actions or access data for which they have explicit permission. Data Access Control will also be a focus, where we'll explore strategies and mechanisms to ensure that users interact only with authorized data, safeguarding both the integrity and confidentiality of information within systems.
Altogether, Authentication, Authorization, and Data Access Control create a comprehensive security framework essential for protecting digital assets and user data across applications and platforms.