In the age of data breaches, API security is not just a best practice; it's a fundamental requirement.
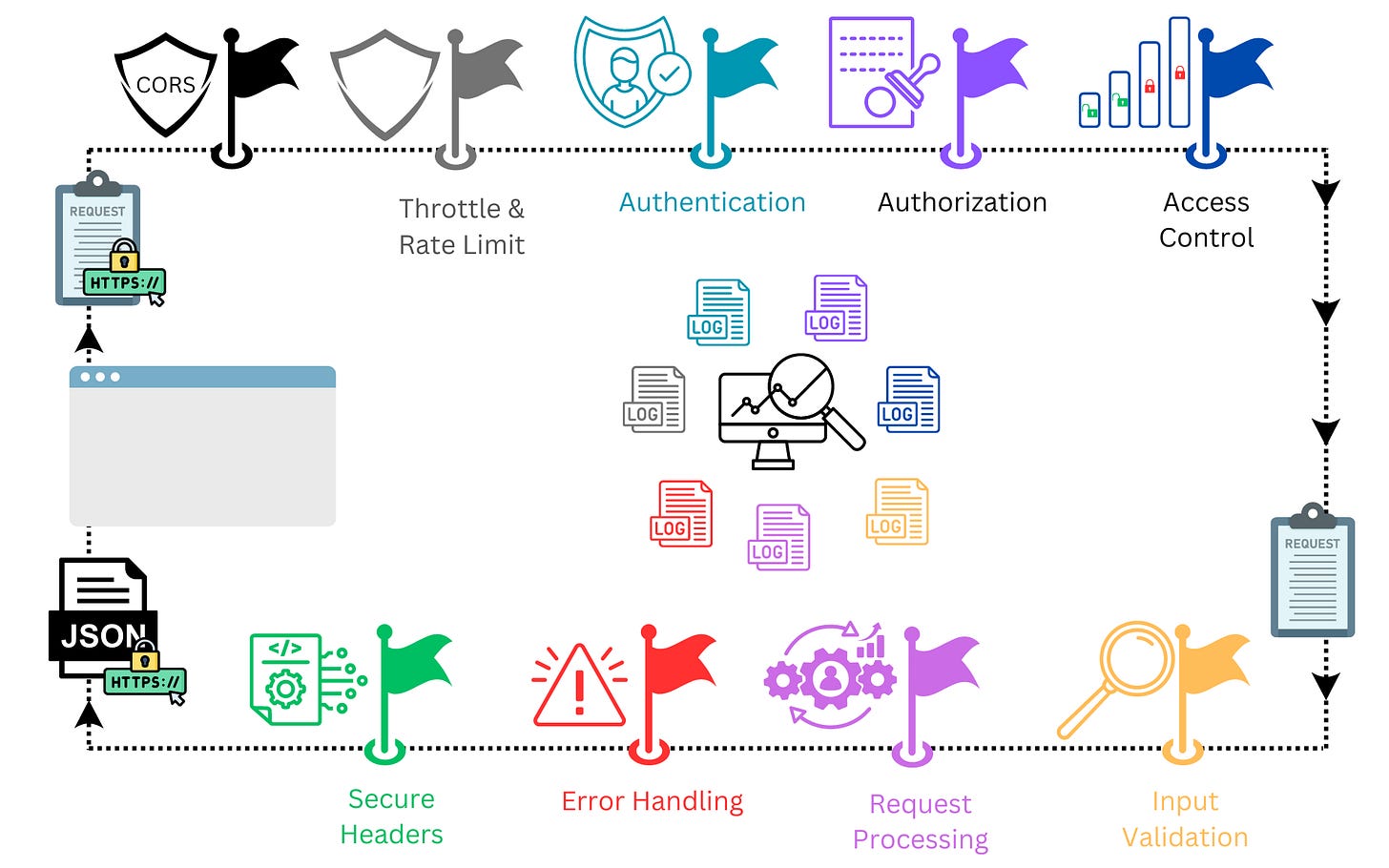
API security is paramount for protecting application programming interfaces (APIs), which serve as the communication bridges between software applications. In the realm of modern web services, API security is non-negotiable. In this comprehensive guide, we will delve into the crucial facets of API security, including authentication, authorization, access control, input validation, error handling, secure headers, and more. Join us on this journey to fortify your APIs and shield your digital assets from potential threats.
Essential API Security Practices
The key security concerns in API security revolve around the three As: Authentication, Authorization, and Access Control. These elements are crucial for safeguarding APIs from unauthorized access and misuse.
Authentication verifies a user or system's identity accessing an API, essentially asking, "Are you who you claim to be?" Methods of verification include API keys, OAuth tokens, JWTs (JSON Web Tokens), and basic authentication (username/password), aiming to allow only legitimate access as the primary defense against unauthorized entry.
Authorization defines the actions a user is permitted to perform, focusing on "What can you access or modify?" It involves roles (e.g., admin, user, guest) and permissions (rights to read, write, delete data, etc.), often managed through access control lists (ACLs) or detailed policies. Its goal is to restrict users to actions or data access they're explicitly allowed, based on their role or specific permissions.
Access control answers "Which records can an authenticated user access?" It ensures users or systems access only data they're meant to, based on roles, permissions, and other criteria. Essential for data segregation, it guarantees users access only necessary information. This is critical in multi-tenant systems, ensuring data relevance per authorized tenant. Strict access control mechanisms are also mandated by many regulations to protect sensitive or personal data.
These practices are vital for managing API access and usage, preventing unauthorized access to sensitive data or features. Data protection laws often demand stringent authentication and authorization to safeguard data privacy and security.
Stay tuned for detailed discussions on each of the three pillars.
Vital API Security Measures
Input Validation is crucial for maintaining data safety and integrity in API interactions. It involves verifying user or system-provided data against expected formats, types, and contents before processing. This measure helps thwart various security threats, notably SQL injection attacks, by filtering out malicious inputs aimed at exploiting the database. Effective input validation enhances user experience through immediate feedback on non-compliant data and is often a compliance requirement in data protection regulations.
Key input validation strategies include:
Type Checking: Ensuring data matches the anticipated type (e.g., integers, strings).
Format Validation: Verifying data adheres to a specified format (e.g., YYYY-MM-DD for dates).
Length Checking: Preventing input data from surpassing set lengths to avoid buffer overflow attacks.
Range Checking: Making sure numerical or other data types are within acceptable limits.
Content Whitelisting: Accepting only pre-approved content, focusing on permitting safe content over blocking harmful content.
Special Character Handling: Neutralizing or omitting special characters to prevent injection attacks.
Encryption transforms readable data (plaintext) into a secure format (ciphertext) that's only accessible with the correct decryption key. This practice is vital for safeguarding sensitive information from unauthorized access, crucially during internet transmission (data in transit) and when stored (data at rest).
For data in transit, Secure Sockets Layer (SSL) or Transport Layer Security (TLS) protocols are used. These protocols encrypt data moving between a user's device and the server, making any intercepted data unreadable. Common applications include HTTPS for web traffic, TLS for email, and VPNs for secure remote connections.
For data at rest, encryption is applied using algorithms like AES and RSA to secure files, databases, and storage mediums, with strict access control to decryption keys. This dual approach ensures comprehensive protection for sensitive data both during transmission and while stored, defending against unauthorized access and breaches.
Encryption Challenges and Considerations
Managing the encryption and decryption keys securely is essential. Ineffective key management can result in data breaches or unauthorized access.
Encryption introduces computational overhead, which might affect the performance of systems and applications.
Compliance with legal and industry standards (like GDPR and HIPAA) is necessary, requiring adherence to encryption best practices and standards to meet regulatory obligations.
Rate Limiting and Throttling are essential practices for managing the flow of incoming requests to APIs, crucial for upholding the service's reliability, efficiency, and security.
Rate Limiting caps the number of requests a user, IP, or client can issue within a specified timeframe, aiming to prevent service overload or DoS attacks. It's typically enforced through algorithms like fixed window, sliding window log, or token bucket, with HTTP 429 Too Many Requests status returned upon limit breaches.
Throttling dynamically modulates API traffic rates based on current load or set thresholds to manage resource consumption. It temporarily reduces service speed for some users, ensuring the API's availability and responsiveness. Throttling can vary by user, service level, or globally, adjusting in real-time to system performance.
Both strategies are vital for:
Fair Use Policy: Guarantees equitable API access, preventing service monopolization.
Cost Control: Manages operational expenses by limiting resource overuse by few users.
Operational Stability: Ensures API reliability and performance by operating within capacity limits.
Best Practices:
Transparent Policies: Clearly communicate rate limits to users for effective consumption management.
Flexible Limits: Tailor limits to API capacity, operation criticality, and user specifics.
Monitoring and Alerts: Use monitoring for usage trends and alerts for approaching or exceeded limits.
Graceful Handling: Respond with clear error messages and headers indicating rate limit status and retry times.
Secure headers are HTTP response directives that instruct browsers on securely processing a website's content, crucial for safeguarding against common web vulnerabilities like Cross-Site Scripting (XSS) and clickjacking.
Content Security Policy (CSP): Aims to thwart XSS attacks by limiting resource loading sources and types. Implemented via the
Content-Security-Policyheader, it establishes a whitelist of acceptable content sources, enhancing script, style, and image security.X-Content-Type-Options: Prevents browsers from MIME-sniffing a resource's content type, mitigating attacks exploiting MIME type guessing. The
X-Content-Type-Options: nosniffheader ensures adherence to the specified content type.X-XSS-Protection: Provides a layer of XSS defense, especially in older browsers, though Content Security Policy (CSP) is recommended for modern applications for more comprehensive protection.
Referrer-Policy: Dictates how much referral data is included with requests, controlling privacy and data leakage through the HTTP Referer header.
Feature-Policy: Enables sites to specify which browser features and APIs can be used, further securing the web environment by limiting potential vectors for exploitation.
While many secure headers are available, not all are necessary for every scenario. Choosing the right set of headers enhances security without compromising user experience. Incorrect configuration, however, can introduce usability issues. For a comprehensive guide on secure headers and their implementation, the OWASP Cheat Sheet series provides valuable insights: OWASP HTTP Headers Cheat
Cross-Origin Resource Sharing (CORS) is a security mechanism in web development that controls how applications from one origin can access resources from another origin, essential for maintaining the integrity and security of web services. It allows servers to define access permissions and conditions, effectively bypassing the browser's Same-Origin Policy under specific scenarios.
Key Components of CORS:
Access-Control-Allow-Origin: Determines which domains can access server resources.
Access-Control-Allow-Methods: Lists the HTTP methods (e.g., GET, POST, DELETE) permitted for resource access.
Access-Control-Allow-Headers: Specifies acceptable headers in requests to the server.
Pre-flight Requests: Utilizes the OPTIONS method to verify the safety of non-simple requests before actual transmission.
Best Practices for CORS Implementation:
Use Restrictive Access-Control-Allow-Origin: Limit access to trusted domains instead of allowing all with
*.Define Specific Methods and Headers: Precisely specify allowed methods and headers, avoiding a blanket allowance.
Maintain Secure Configuration: Periodically update CORS policies to adapt to new security threats and changes in your application environment.
Effective error handling in APIs is crucial for balancing usability for legitimate users and security against potential attackers. It involves managing errors to provide necessary feedback without revealing sensitive details that could aid malicious activities.
Key Principles of Secure Error Handling:
Generic Error Messages: Use broad error messages that inform users of an issue without disclosing specifics about the backend, like database types or software versions. For instance, replace detailed error messages with general ones like "Invalid input data" to avoid exposing system vulnerabilities.
Consistent Error Responses: Maintain a uniform format for all error messages, incorporating standardized error codes or messages that can be easily understood by the client application without divulging too much information.
HTTP Status Codes: Utilize HTTP status codes effectively to convey the nature of the error, using codes like 404 for not found, 400 for bad requests, 403 for forbidden access, and 500 for internal server errors. This strategy abstracts the application's internal details while providing clear communication.
Log Detailed Errors Server-Side: While keeping client-side error messages generic, log detailed errors on the server. This approach facilitates debugging and monitoring for security threats without compromising sensitive information.
Rate Limit Error Notifications: To thwart attackers from employing automated tools to elicit errors for gathering API insights, apply rate limiting to error messages.
Input Validation Errors: Communicate input validation errors clearly to assist users in correcting their requests, but avoid providing information that could be exploited for injection attacks.
Monitoring and logging are vital for securing APIs, enabling the tracking, analysis, and management of usage data and activities. This practice is crucial for understanding API utilization, spotting anomalies, and identifying potential security threats, allowing for swift responses to malicious activities, operational issues, and compliance matters.
Best Practices for Monitoring and Logging:
Standardized Format: Ensure all logs adhere to a uniform format, simplifying analysis and filtering for more efficient issue resolution and insight gathering.
Comprehensive Coverage: Log all relevant API aspects, including authentication events, access control decisions, administrative actions, and errors, to provide a full picture of security-relevant activities.
Secure Storage: Safeguard log data against unauthorized access and tampering, potentially through encryption and strict access controls to enhance data integrity and confidentiality.
Regular Review: Establish routines for frequent log examination to detect signs of suspicious behavior, which is fundamental for proactive threat mitigation.
Automated Analysis: Leverage automated tools for real-time anomaly and potential security incident detection, facilitating immediate response to emerging threats.
Retention Policies: Develop clear policies for log data retention, balancing the need for historical insights with considerations for storage management and privacy requirements.
Additional API Security Considerations
Security Testing and Audits play a pivotal role in API security, ensuring adherence to security standards and regulations. These practices involve a meticulous evaluation of the API, its endpoints, and associated infrastructure to pinpoint vulnerabilities, misconfigurations, and compliance shortcomings that might be exploited by malicious actors.
Caching Controls utilize HTTP headers to govern the caching of web server responses by browsers and intermediary proxies. These mechanisms are essential for enhancing performance by alleviating server load and reducing latency. However, they require diligent management to prevent the exposure of sensitive information to unauthorized users or insecure storage practices.
Caching control relies on essential HTTP headers to define policies that optimize performance while ensuring security:
Cache-Control: This primary header offers directives for caching mechanisms, including
no-store(prevents storage in any cache),no-cache(requires validation before releasing cached copies),private(for single-user use), andpublic(cacheable by any cache).Expires: Specifies an absolute expiration time for cached resources, although modern caches prefer
Cache-Controldirectives.Expiresis maintained for backward compatibility.ETag/If-None-Match: Allows cache validation by the origin server, ensuring the cached version remains current.
ETagprovides a unique resource version identifier, whileIf-None-Matchconveys theETagvalue to the server for validation.Vary: Instructs caches regarding request headers that distinguish one cache entry from another. Vital for applications serving varied content based on headers like
Accept-LanguageorUser-Agent.
Regular updates and patches are foundational practices involving the systematic maintenance of software and systems to shield against identified vulnerabilities. This practice is instrumental in upholding the security and resilience of IT ecosystems, encompassing APIs, applications, operating systems, and various infrastructure components.
Importance of Regular Updates and Patches:
Closing Security Gaps: Hackers and cybercriminals frequently target known software vulnerabilities. Routine updates mitigate these risks by patching vulnerabilities, lowering the chances of unauthorized access and data breaches.
Compliance: Many regulatory frameworks mandate keeping systems current as a compliance requirement. Consistent patching is indispensable for meeting standards like GDPR, HIPAA, and PCI DSS.
Stability and Performance: Updates not only address security concerns but often enhance system performance and reliability.
Protecting Sensitive Data: Securing software and infrastructure against recognized vulnerabilities is paramount to safeguarding sensitive customer and business data from exposure or theft.
Conclusion
In this comprehensive journey through API security practices, we've covered essential strategies that directly impact the safety of your digital environment. Whether you're a developer, IT professional, or simply concerned about data security, these practices are fundamental for ensuring the protection and integrity of your APIs.
From input validation to encryption, rate limiting, secure headers, CORS, effective error handling, monitoring, logging, and caching controls, each practice has a role to play in enhancing your API's security. They collectively form a robust defense system against a variety of threats.
Always remember, API security is an ongoing journey. By implementing these practices, staying informed about emerging threats, and adapting to the ever-evolving cybersecurity landscape, you take an active role in fortifying your API infrastructure. Your commitment to security ensures that your digital environment remains safe, reliable, and protected for you and your users.